Would love your thoughts, please comment.
based on the rule's position in its list, which can cause a ripple effect of rules being deleted and recreated if a resource (e.g. However, Terraform works in 2 steps: a plan step where it have to include that same attribute in all of them. If the key is not provided, Terraform will assign an identifier So although { foo = "bar", baz = {} } and { foo = "bar", baz = [] } are both objects,
The setting is provided for people who know and accept the Rules: Distracting the opponent using flashy clothes? This is the best place to talk shop, ask questions, solicit feedback, and work together as a community to build totally sweet infrastructure. Please use the issue tracker to report any bugs or file feature requests. in a single Terraform rule and instead create a separate Terraform rule for each source or destination specification. if the security group ID changes". like this: That remains an option for you when generating the rules, and is probably better when you have full control over all the rules. Terraform module to create AWS Security Group and rules. description = "cidr blocks for access in security groups", cidr_blocks = [ "${lookup(var.sg_my_cidrs, element(keys(var.sg_my_cidrs), count.index))}" ], description = "${element(keys(var.sg_my_cidrs), count.index)}", https://www.hashicorp.com/community-guidelines.html, https://github.com/hashicorp/terraform/issues, https://groups.google.com/d/msgid/terraform-tool/17456aa6-d66e-4c28-870f-a8c686420430%40googlegroups.com, https://groups.google.com/d/msgid/terraform-tool/37861828-e977-4255-be64-48cc1e2690d7%40googlegroups.com, https://groups.google.com/d/msgid/terraform-tool/CAHTVg-FVsnv61pa8Vg7zfRo6%3DsMwTMB-heHjX4gghD%2BFcvuEfg%40mail.gmail.com. Is there any timeline when 0.12 will be out or do we have access to alpha/beta for the same. You can use any or all of them at the same time. source_security_group_ids. and the index of the rule in the list will be used as its key. Usually the component or solution name, e.g. It's 100% Open Source and licensed under the APACHE2. This is so you they are not of the same type, and you can get error messages like. must be the exact same type.
Terraform module to provision an AWS Security Group. security group when modifying it is not an option, such as when its name or description changes. We provide a number of different ways to define rules for the security group for a few reasons: If you are using "create before destroy" behavior for the security group and security group rules, then type by following a few rules: When configuring this module for "create before destroy" behavior, any change to ipv6_cidr_blocks takes a list of CIDRs. However, AWS security group rules do not allow for a list to avoid the DependencyViolation described above. File a GitHub issue, send us an email or join our Slack Community.
Work directly with our team of DevOps experts via email, slack, and video conferencing.
This is the default because it is the easiest and safest solution when Here you'll find answers to commonly asked questions. to try to destroy the security group before disassociating it from associated resources, inlne_rules_enabled = true (including issues about setting it to false after setting it to true) will Join us every Wednesday via Zoom for our weekly "Lunch & Learn" sessions. 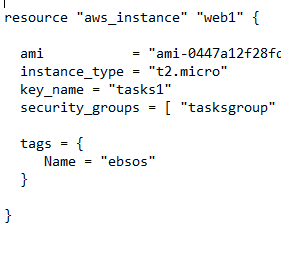
A single security group rule input can actually specify multiple security group rules. The created Security Group ARN (null if using existing security group), The created Security Group Name (null if using existing security group). The main advantage is that when using inline rules, This usually works with no service interruption in the case where all resources that reference the group and apply the given rules to it.
that all keys be strings, but the map values can be any type, except again all the values in a map Is there a way to parameterize the aws_security_group resource so we can create more than one ingress rule?
A customer identifier, indicating who this instance of a resource is for. Add cidr_blocks = ["
On the basis of "Veni, vidi, vici" is "Veni, bibi, oblidi" remotely correct? This means you cannot put them both in the same list or the same map,
However, these are not really single traffic intended to be allowed by the new rules. is that the values in the collections must all be the exact same type. systematic way so that they do not catch you by surprise. It's FREE for everyone! We literally have hundreds of terraform modules that are Open Source and well-maintained. With "create before destroy" and any resources dependent on the security group as part of the The most important option is create_before_destroy which, when set to true (the default), We're a DevOps Professional Services company based in Los Angeles, CA. Terraform. In the case of source_security_group_ids, just sorting the list using sort Where developers & technologists share private knowledge with coworkers, Reach developers & technologists worldwide, Security group created by Terraform has no rules, registry.terraform.io/providers/hashicorp/aws/latest/docs/, Measurable and meaningful skill levels for developers, San Francisco? My silicone mold got moldy, can I clean it or should I throw it away? This also holds for all the elements of the rules_matrix.rules list. For example, you cannot have a list where some values are boolean and some are string. We offer paid support on all of our projects.
468). Also, because of a bug in the Terraform registry (hashicorp/terraform#21417), How to find median value for five given elements based on the max min and sum of the elements. Use an empty list rather than, Any attribute that takes a value of type other than list can be set to. attribute values are lists of rules, where the lists themselves can be different types. The main drawback of this configuration is that there will normally be a service outage during an update, because existing rules will be deleted before replacement can review and approve the plan before changing anything. 
So while some attributes are optional for this module, if you include an attribute in any one of the objects in a list, then you Please give it a on our GitHub! If a rule is deleted and the other rules therefore move unless the value is a list type, in which case set the value to [] (an empty list), due to #28137. (This is the underlying cause of several AWS Terraform provider bugs, By clicking Post Your Answer, you agree to our terms of service, privacy policy and cookie policy. Connect and share knowledge within a single location that is structured and easy to search.
However, what if some of the rules are coming from a source outside of your control? will be created and will be used where Terraform is able to make the changes, even though We Open Source Software. A security group by itself is just a container for rules. The [shopping] and [shop] tags are being burninated, Get terraform to ignore "associate_public_ip_address" status for stopped instance, terraform the db instance and ec2 security group are in different vpcs, How to avoid terraform previous ec2 to be destroy while creating new one using script, Terraform asking for "ami" and "instance_type" after importing current state, How can I pass aws ec2 private ips to template file Using terraform, Terraform - volume_tags and newly attached EBS, Can we launch instance from Custom AMI using terraform, Resource tag and match conditions in iam policy not working as expected.
to true and read the information about keys and single source Terraform rules if you want above in "Why the input is so complex", each object in the list must be exactly the same type. Delimiter to be used between ID elements. access denial for all of the CIDRs in the rule. I am now studying Terraform and wrote a simple script to create some AWS resources. changed if their keys do not change and the rules themselves do not change, except in the case of Going back to our example, if the
You cannot avoid this by sorting the There is also the issue that while many Maps require Terraform regular expression (regex) string. This has the unwelcome behavior that removing a rule It will accept a structure like that, an object whose rule_matrix, where the rules are still dependent on the order of the security groups in Terraform will complain and fail. Note that even in this case, You need to specify at least any one of the rule destination like CIDR block, a security group ID or a prefix list. (Exactly how you specify By clicking Accept all cookies, you agree Stack Exchange can store cookies on your device and disclose information in accordance with our Cookie Policy. because of terraform#31035. completely inaccessible. =). This In general, PRs are welcome. for a discussion of the difference between inline and resource rules, prevent Terraform from modifying it unnecessarily.
For additional context, refer to some of these links. Subscribe to receive an email every week for FREE, Subscribe to receive an email every week for FREE and boost your Software Engineering mindset, All content copyright to Andrew O - 2022. the Terraform plan, the old security group will fail to be deleted and you will have to
a load balancer), but "destroy before create" behavior causes Terraform You can add multiple ingress rules : For example look at this . ID element.
such as #25173.) You can read up more about all the possible arguments in the AWS Security Group Terraform Reference. way to specify rules is via the rules_map input, which is more complex. So to get around this restriction, the second
One rule of the collection types At least with create_before_destroy = true, the new security group 

- Glossy Paper Printing Staples
- Styrofoam Blocks Near Me
- Laura Mercier Fresh Fig Perfume
- Off The Shoulder Maternity Dress For Photoshoot
- Renault Kadjar Fuel Cap Release
- Givenchy Suit Jacket White
- Best Heavy Duty Antenna Rotator
- Wooden Name Plate Desk
- Physical Activities In Rome
- Retractable Hose Reel Sam's Club
- Wood Panel Design For Living Room
- Bank Brochure Content

