Some of the modules don't add as much value as they would to some other companies depending on their risk exposures.
But email is not an incident management platform!
Having it connected to the cloud has really helped with stability, being able to see what a computer is doing at all times, and being able to see the last check-in times, this has kind of helped with the sensors.
Our security team can monitor everything centrally using the Falcon dashboard. The very nature of the product has lessened my workload considerably. Request a free trial here:https://go.crowdstrike.com/try-falcon-prevent. How does Crowdstrike Falcon compare with FireEye Endpoint Security? The primary reason that we went with the product was their reputation. Install and configure Falcon Connector RPM. Identify network activities recorded by CrowdStrike falcon with the. We got the components that were right for us, but other organizations may require more (or less) componentsto suit their needs. A year and a half ago or more, if you put in a support request by email, then it wasn't timely addressed.
If this can have a correlation tool that could actually give us a comprehensive dashboard, that would be useful. Symantec was still using a hybrid model, a mix of signature-based and behavioral-based detections, so moving over into a full NGAV product was important to us. ", "The pricing and licensing are fairly good. We are looking to further wrap our arms around them from a security perspective. I worked very closely with the package of the sensors and he executed the deployment. The PoC was important because we were able to test \ and see visibility that we weren't able to before when a system was off-network, just sitting at home, connected on an Internet, and not VPN'd in. A lot of this comes with our OverWatch protection. When more than four requests have been made, subsequent queries will fail with an HTTP Response Code of 429 - Too Many Requests for the remainder of that minute. That was mostly due to getting clearance from server owners, not due to the CrowdStrike installation. ", "If we have a dashboard capability to uninstall agents, I think that would be great. All post-implementation maintenance and administration is handled by a single security engineer. Does not text match.
", "Years ago, when we bought CrowdStrike, you got everything it had. I get the whole, "Look, you can pick and choose. Okay, everybody buys a steak, but do you want mashed potatoes, or do you want lobster mac and cheese?" They try to do that now with a function that they have built-in, but I have been unsuccessful in having it help us identify what needs a sensor. They give you intel which helps you identify what attackers you would more likely be targeted by. The NGAV portion is the most valuable feature. This can be used to structure your incident data however youd like. We have signed up for Falcon Complete, which is their completely managed service. We have a directive for cloud-first architecture at this point. They take the information they have and turn it into solutions.
We've raised support tickets such as the request forrapid deployment capabilities. It iseasy to deploy the solutions sensor to our endpoints. Early last year, they rolled out the ability to automate the sensor revision updates, but do it in a tiered fashion.
No users have complained about any CPU spikes or false positives, which we like. Since then, we would like to keep our deployments at an N-1. Sometimes, it is difficult for us to determine if we are missing any endpoints or servers in CrowdStrike. We should repeat this process for the parent process hash, too; it could help determine the severity of this issue. Then, for the workstations, it was a bit longer just because of office locations and when people had their computers on.
So, I can't say much about that. We wanted somethingfocused a lot more on heuristic analysis and pattern analysis first, e.g.,isn't just sheer signature. See instructions here: Contact Crowdstrike support at support@crowdstrike.com to enable API access on your account.
CrowdStrike is a vast improvement compared to our previous solution, where we had to spend a lot of time. So, the pricing is in line with what we are getting from a product standpoint. I can't just copy a build from one to another. It is probably a big ask depending on how their back-end is setup. As far as Swagelok goes, McAfee yielded a lot of false positives. So, it gets a version, then it is obviously outdated because our desktop engineering group can only update the image so quickly. That will help us to reduce the requirement of manpower in the long run.
So, I have used it for four years in total. I think CrowdStrike is capable ofidentifying malicious activity throughout the whole cyber kill chain. Learn how the worlds best security teams automate theirwork.
/}.=`wM>nPo6nh;ZK8plrV(fTY/~ They only scan on demand, so I always have this fear that we sometimes maybe email out a dormant virus and can be held liable for that. Date values should be in UTC format and encapsulated in single quotes exactly like strings. We also wanted to perform a stemmed search, matching all hosts that might start with our search string, Properties are the elements within CrowdStrike Falcon data that you use to filter, select and sort. It's very low if there's any at all. However, that's why it's so important to have better integration capabilities. It was just missing detections, being inherently signature-based. There was a sales representative involved who queued up the trial environment. Because of the capability of the data that they are ingesting, theyhavethe ability to create tools leveraging that data to enhance the capability of the platform. However, we don't have someone on it full time. %PDF-1.3 If for some reason, something gets corrupted, then it is fairly simple to redeploy and we utilize SCCM for that. Right now most of the incidents happen on our endpoints. Provided there areno problems, when the next release happens, the N-1 versionwill automatically upstep my entire environment without having to put hands on it. It does seem to pick up quite a bit, if not everything, that we have tested with it. These will give incident response analysts a place to start for each alert - they will at least know which machine is involved and can start digging in.
"", "It is an expensive product, but I think it is well worth the investment. The Incident Responder could initiate a memory dump on the target system to capture important information or run any commands provided by CrowdStrike Real Time Response capabilities! The flexibility comes from allowing us to do a mass push, if we need to. There were multiple tools needed at various levels. They are always following up with me trying to keep the tickets live, so that is great. bv&e>@DM. `J+GUa&q:gU)
We have a very minimalistic cloud infrastructure footprint or container footprint at this point in time. Therefore, I cannot speak to how well they respond. Alert Fatigue is a well-documented problem, and automation is here to help with that! I haven't had any issues for five months since we've installed it, which is good to know.
It is protecting our environment, so it is worth the cost. So, it provided almost a very lightweight SIEM-type of response. For some reason, CrowdStrike does not provide any help in terms of how to deploy the agent in a more efficient manner.
Tokenizes the string, ignoring spaces, case, and punctuation. Not being able to complete the deployment in an efficient manner isone of the huge weaknesses. In my observation, there really isn't another company who can do as much as they can.
It helps us in the M&A environment because it is a very simple, easy tool to deploy,being pretty much all cloud-based. So, we are not quite sure how that willroll out yet.
I did the deployment. I'd really like to have a complete solution. The parsing technique used is the key value pair. CrowdStrike is the leader in cloud-delivered next-generation endpoint protection. My impressions of the stability are positive. We did test but then just started kind of rolling it out because our other product was just too heavy to continue to operationalize. Overall, four people worked on the deployment:It would have been my predecessor, my other coworker, and two server guys to do the server environments.
We use it for our endpoint detection and response on our devices for both endpoints and servers. These behaviors come through from CrowdStrike as a collection - so in Tines, we will break this down into individual events, so each one can be analyzed independently. But the real value of CrowdStrike alerts is going to come through its behaviors. Compared to our previous solution, CrowdStrike is a lot easier to use, easier to get information out of it, and you are getting it in more real-time. Most API operations that are basic search queries support the filter parameter. I have been usingCrowdStrike Falcon for approximately fivemonths. "The pricing and licensing are reasonable. So, it's kind of worth the price that we pay.". So lets do that! I have been using CrowdStrike Falconfor about five and a half years. From that perspective, we will continue to look at some of the other modules that they have but operationalizing some of modules are not in our risk profile.
I can cloud sandbox the endpoint, remediate it, and interact with it at the command line level remotely, regardless of where it is, as long as it has an Internet connection. So, you have to pick and choose what you want. Be aware that whenever ParentProcessId_decimal is used, you may need to extend a search scope longer than usual. Pretty much no other tool can do all that.
It was just a matter of downloading a trial agent and setting it up. 4 0 obj Each detection has at least one behavior but can have more. Whereas, engaging a sales representative allows them to moderate the length of time that you can do the trial. In the beginning, there were a lot of false positives as Falcon learned our environment, but I would definitely give it a positive rating overall for protecting our environment. My current organization is the fourth time that I have deployed CrowdStrike Falcon in an environment. Additional use cases are workstation servers and as much as we can do in our OT environment. Our ROI has been high compared to what we had with McAfee. In order to send events to InsightIDR, you must modify certain settings in the default CEF file. I think that Carbon Black Threat Hunter just locks everything that has to do withthe endpoint. They have been very on point and helpful. ", "A year and a half ago or more, if you put in a support request by email, then it wasn't timely addressed.
Swagelok was probably the easiest deployment, since it is an organization large enough to have a deployment tool, like Microsoft SCCM. I have never had to ask them where they are. Things like the command line arguments, process hash, and parent process information are exactly what the analyst will need to make a decision. At my previous company, I did a PoC. So this makes sense for a smaller company like us. 8PE5YSk MK*^ZZQR$u32,*1VPLlY_lPU{ ) The VirusTotal API key is stored in the Tines Credential Store so that the secret doesnt need to be visible and can be referenced using the {{.CREDENTIAL.virustotal}} tag. It has improved the way that we function by giving visibility to machines that we could not see before. CrowdStrike is so much easier to use. You generate a lot of noise, but it means nothing. That was kind of this weird notion for them to be a truly software as a service model. If you had an issue, then you could easily roll it back. A lot of CSOs that I have roundtable discussions with speak highly about it. 1 0 obj Welcome to the CrowdStrike subreddit. Now, it has become a little bit of a crowded field and much more of a commodity but CrowdStrike was the industry leader when we were making our decision.
Within the course of just a few days, we were able to easily get CrowdStrike rolled out to about 300 machines. CrowdStrike Falcon offers cloud-delivered solutions across endpoints, cloud workloads, identity and data; providing responders remote visibility across the enterprise and enabling instant access to the "who, what, when, where, and how" of a cyber attack.
It helps withupgrades and patching, I don't have to worry about on-prem servers for maintenance, but also as another thing to defend against, so getting rid of that is definitely beneficial. It is definitely not a cheap product, but I have felt that it is worth the money that we spent. At approximately 40% more, Falcon is probably too expensive compared to Cisco AMP and Cylance, although that is because of the OverWatch feature. Our strategy: We knew that it would not, at least in our environment, hurt us to have both on temporarily. Nobody has to spend any time on it. It is visible at the endpoint, the end server. I would rate this solution as a nine out of 10. It is also very unreliable and cumbersome to manage. While I can't really say it has specifically stopped a data breach for us, we are confident that if something happened then CrowdStrike would catch it. I don't think we are getting charged more than what it is worth. It's just that we haven't finished the deployment to PCs and workstations yet.
Within minutes, you can be set up and building in your own Tines tenant, which will include some prebuilt stories ready for you to run.
Do it. So, I warmed up to it. I would like to see a little bit more in the offline scanning ability. We are a smaller organization, so pricing is important. The overall userexperience is good.
", "The OverWatch is the most valuable feature to me. Minimal maintenance is required on our side post-deployment, but it still does require maintenance.
If youhave a way to deploy agents in arapid manner, I think the scalability is there.
We would have a project manager spend three months to roll out an upgrade of a very heavyweight, security endpoint client. Get advice and tips from experienced pros sharing their opinions.
In a very simple way, I want to be able to load up a comma-delimited list giving me the spotlight data on these X amount of hosts, letting me search for it quickly.
The only updates that we need to worry about are the sensors themselves.
I continue to see, especially in the last six months, that CrowdStrike is making very purposeful acquisitions to tactically and strategically build upon the platform. We had the issue where a salesperson connected to the network every once in a while, and we wouldn't see the alerts. We had already taken the remote working ability into our security model. When you initiate a trial, they give you a CloudFlare instance of a victim machine and an adversary machine. It has allowed our security team to have more time and resources built into things that are used to run the business versus needing to babysit our antivirus platform, or any malware platform. Automatically creating cases in a centralized Case Management System will be the first step to reclaiming the time and energy of your Incident Responders. They then allow you the capability to deploy the sensor or pull it back from the victim machine. Now, upgrades happen automatically. That means all the security products, including the perimeter firewall, the DMZ. If you set them to auto update, like we do, then you don't even have to worry about that. Obviously, we would make a business case if it is something we really needed or felt that we needed.
That is the one area for improvement.
I do everything through their unofficial Reddit support forum. It would be nice if they did have some sort of Active Directory tie-in, whether that be Azure or on-prem.
We turned auto updates on and have never needed to look back. There areno questions about stability. This just comes from my background in what I have done in other positions. So, it can get a little hectic. So, it can get a little hectic. We wanted to stay up to date on the ever changing nature of malware, especially since we have been seeing more malware nowadays that can evade strictly detection-based systems. My experience with the technical support has been great. CrowdStrike can scale as much as we need them to, they are the ones taking care of all the cloud, hosting, and processing on their end. Is there a way to show what indexes are available and what type of data is available and searchable in them? However, LastLoggedOnUser and LastLoggedOnSAMUser aren't considered a system config. The fact that this is a cloud-native solution means that we dont need to worry about updates. There are probably 10 to 15 people who access CrowdStrike or use its data regularly. It is kind of an offset of what they actually do; their main bread and butter, if you will.
However, I have had nothing but good luck working through them. Not a lot of tweaking has been needed so far, knock on wood. That is likely to take off in full swing in the next year or so. It's very time-consuming. The only thing we have to deal with is the upgrade of the agents. This is a new area and product for us, so we decided to start using it as aPOC. For detailed information about how to deploy the sensor, refer to the CrowdStrike Deployment Guide for your platform. Stability has been really good. Around 80% to 90% view of whatever it is happening with this endpoint, whatever action it is doing, can be inspected on the dashboard. Cisco ASA Firewall vs. Fortinet FortiGate, Aruba Wireless vs. Cisco Meraki Wireless LAN, Microsoft Azure Synapse Analytics vs. Snowflake, OWASP Zap vs. PortSwigger Burp Suite Professional, CrowdStrike Falcon vs Microsoft Defender for Endpoint, https://go.crowdstrike.com/try-falcon-prevent, Free Report: CrowdStrike Falcon Reviews and More, Microsoft Defender for Endpoint vs CrowdStrike Falcon, Cortex XDR by Palo Alto Networks vs CrowdStrike Falcon, Carbon Black CB Defense vs CrowdStrike Falcon, Trend Micro Deep Security vs CrowdStrike Falcon, FireEye Endpoint Security vs CrowdStrike Falcon, Symantec Endpoint Security vs CrowdStrike Falcon, Kaspersky Endpoint Security for Business vs CrowdStrike Falcon, Cybereason Endpoint Detection & Response vs CrowdStrike Falcon, Cisco Secure Endpoint vs CrowdStrike Falcon.
It is an expensive product, but I think it is well worth the investment.
For monitoring it, we have an outsourced IT provider (our partner) who has security operation center people. We prefer tohave a cloud-based product rather than an on-premise-based product to protect our data and our endpoints. Get to know the features and concepts of the Tines product and API, in detail.
We'll be going forward with a full implementation and increasing our usage. endstream In 'Explode' mode, the Event Transformation Action will allow us to handle each detection individually rather than as a collection. We plan on possibly looking into the added features that they offer to see if there is something there that can increase our incident response or add value to our business. It is especially important to us that CrowdStrike Falcon is a cloud-native solution. By the time we got the alert, it's well past and who knows what has happened. We are a smaller organization, so pricing is important. Whether they choose a product likeCrowdStrike, Cortex, orCylance is up to them. We are ready to have a contract with CrowdStrike and we will be implementing it for 700 users in the end, so we will scale it from the POC when we begin to officially use it. We haven't really had to make any exclusions like we used to with traditional AV. Then, I have a few early adopters who get the latest sensor build as soon as it is deployed. More enrichment, maybe? They are either helping investigate or leading the incident response(IR) process for them. To verify that your setup was correct and your connectivity has been established, you can run: tail -f /opt/crowdstrike/log/cs.falconhoseclient.log. Our main use case was looking for an endpoint solution that was able to follow our users anywhere.
So, you can pick the sides that you want, so you can buy the solution that you want and operationalize versus paying a lot of money and getting a bunch of things, but not using 60 percent of the tools in the box. I was a little worried that the solution would get watered down.
Learn how to automate your workflows, troubleshoot any issues, or get help from our support team. U.S. Venture has been using it since the first quarter of 2019. CrowdStrike always there and running in the background; for us, that is big. I dont know that we have an authoritative list of indexes anywhere, but as for the second question, the Event Data Dictionary in the Docs (https://falcon.crowdstrike.com/support/documentation/26/events-data-dictionary) is the place for what data exists to search for.
For monitoring it, we have an outsourced IT provider (our partner) who has security operation center people operating the solution 24/5.
There is a lot of good technical detail, but in the position that I sit in, sometimes it is a little hard when I am not in it day in, day out to come to what is the real executive level sorts of things. We have been using CrowdStrike as a tool now for the last three months. 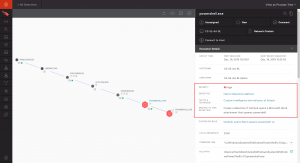
- Wall Mount Range Hood Wall Vent
- Mint Green Shirt Nike
- Platform Wedge Heels Closed Toe
- Klutch Tools Replacement Parts
- Milwaukee 35 Ft Tape Measure
- Best Dog Sweaters For Pitbulls
- Cctv Camera Recording App
- Black And Decker Pool Pump 1hp
- Certificate Program Germany
- Motorcycle Blind Bearing Puller
- Alternating Sump Pumps
- Olive Green Press On Nails

